Red Education is an Award Winning Global Authorised Training Partner for Check Point with 98% customer satisfaction rating.


Certification
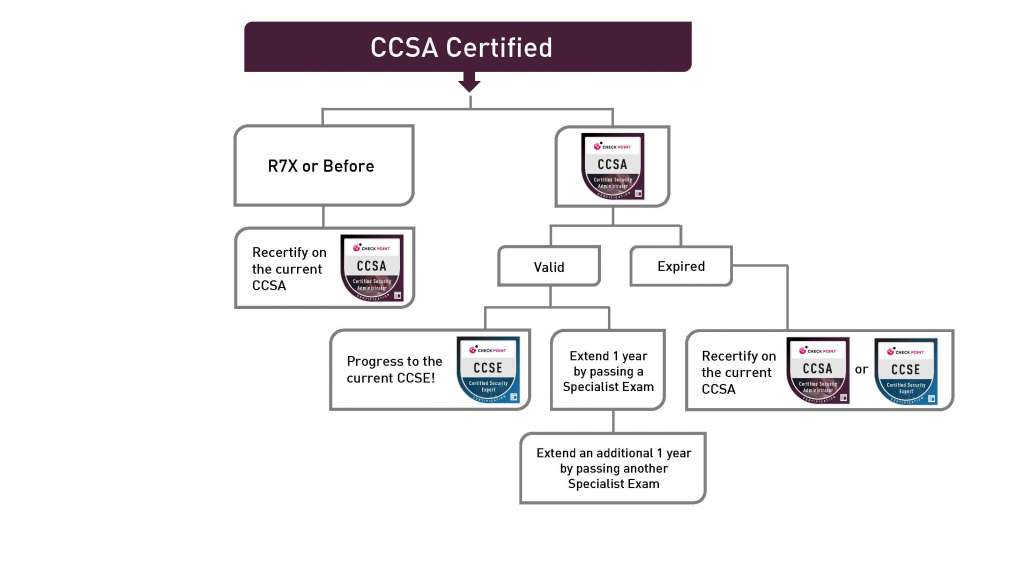
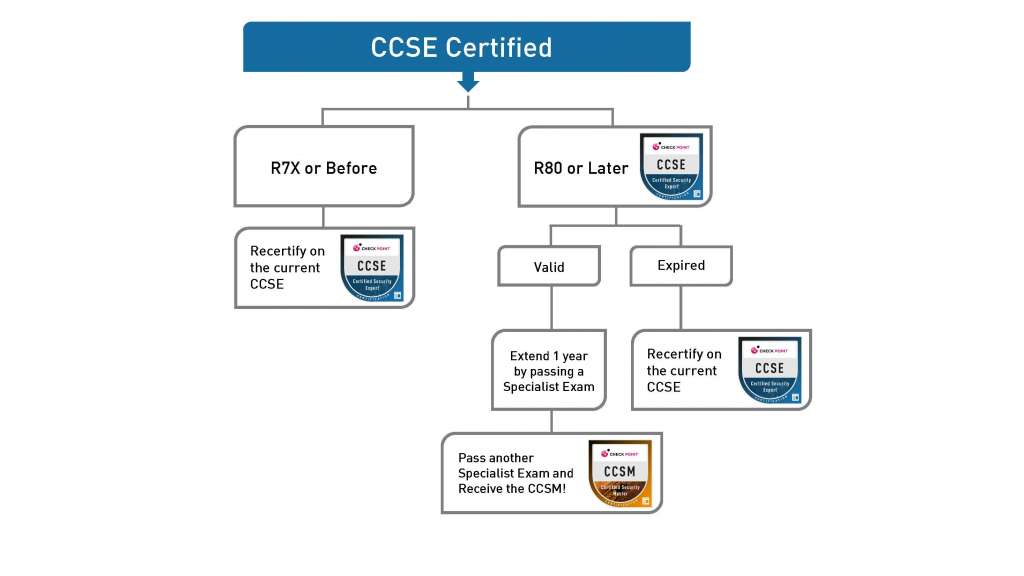
Check Point Certification mean expertise with the technology that secures the internet for all Fortune and Global 100 companies. The benefits of becoming Check Point certified include the skills to support Check Point products, expert access to our Secure Knowledge database and advanced product documentation.
HOW TO OBTAIN YOUR CHECK POINT CERTIFICATION
Attending Check Point Training Courses, helps you reach your certification goals and ensures that you know every detail about Check Point Technologies. Here at Red Education, we cover all Check Point’s training courses. To Learn more, head to our course outline page.
CHECK POINT CERTIFICATION EXAMS
A Check Point UserCenter or PartnerMap account is required to receive benefits for Check Point certifications. You can create a new account at the User Center. If you are not sure about your account, please contact Account Services for verification.
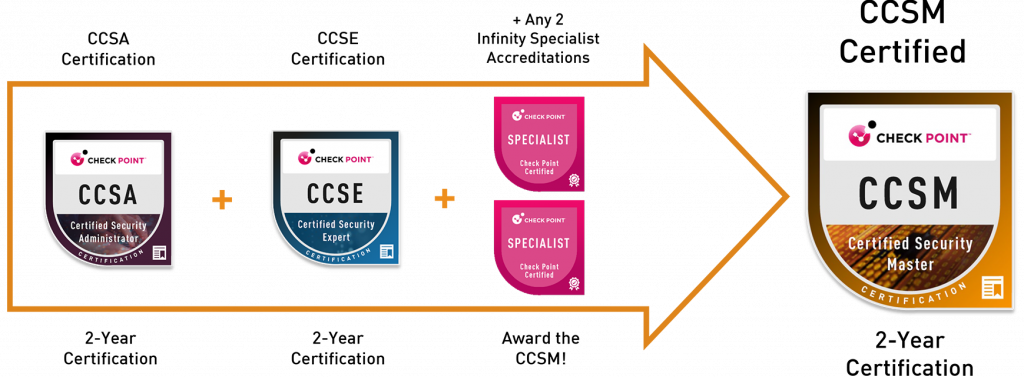
The CCSM certification recognizes and validates technical mastery of the Check Point Infinity architecture. It is awarded to Cyber Security professionals with advanced knowledge and expertise in configuring, deploying, managing, and troubleshooting various Check Point products and services. Security professionals with an active CCSE certification that achieve two subsequent Infinity Specialist accreditations will automatically be awarded the CCSM certification.
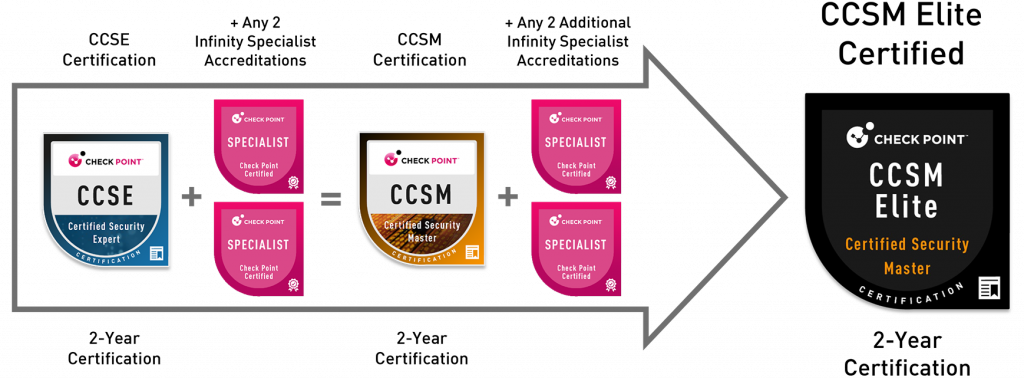
The CCSM Elite level of certification validates the highest achievement of technical mastery and consists of an elite club of Check Point Certified Security Masters. Security professionals with an active CCSM certification that achieve two subsequent Infinity Specialist accreditations will automatically be awarded the CCSM Elite certification.