Red Education has been awarded #1 Authorized Training Partner across JAPAC 10 years in a row, with 98% customer satisfaction rating including GLOBAL Instructor of the Year Award 2021, 2022 and 2023


Recommended Learning Pathways
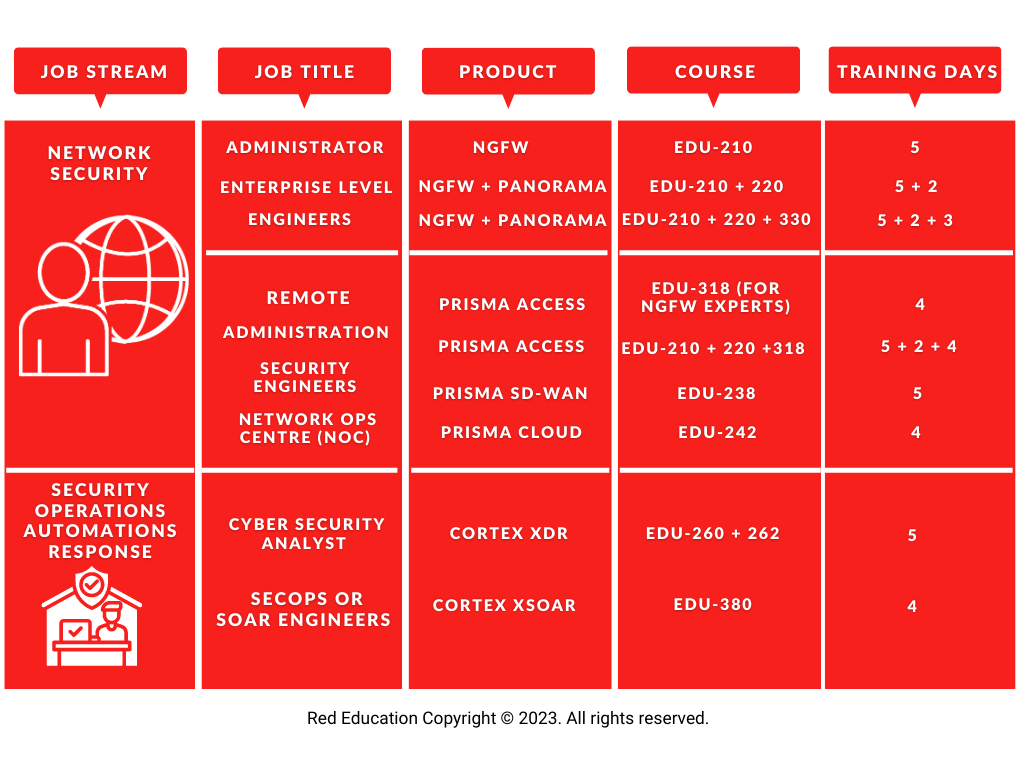
This comparison chart is designed to determine the recommended PALO ALTO NETWORKS courseware training. It is based upon an employee's job function, their specialty within the business, against an organisations existing hardware + cloud topography and cloud security. Upon successful completion of training, it should empower an employee with the necessary knowledge to competently manage architecture firewall configuration security devices successfully within the company's cybersecurity footprint strategy.
Training Credits

Certification
Explore Our Palo Alto Certification Track:
Our Palo Alto certification track is a well-crafted journey that takes you from a beginner to an expert. Whether you're starting as a certified network security administrator or aspiring to become a certified Palo Alto Networks expert, we have the right courses to suit your career goals.
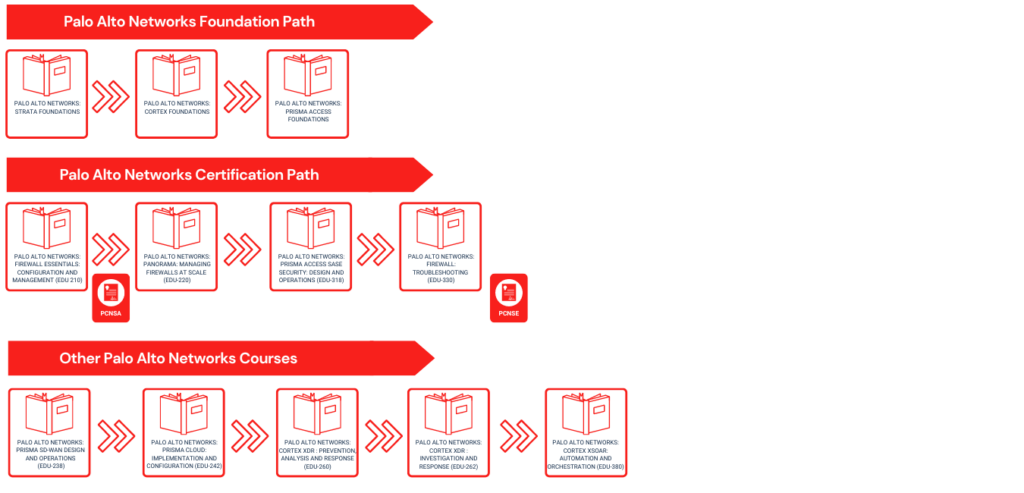
Overview
The PCNSA certification validates the knowledge and skills required for network security administrators responsible for deploying and operating Palo Alto Networks Next-Generation Firewalls (NGFWs). PCNSA certified individuals have demonstrated knowledge of the Palo Alto Networks NGFW feature set and in the Palo Alto Networks product portfolio core components.
Certification Objectives
Palo Alto Networks technology is highly integrated and automated. The Palo Alto Networks product portfolio comprises multiple separate technologies working in unison to prevent successful cyberattacks. The PCNSA seeks to identify people who can operate Palo Alto Networks Next-Generation Firewalls to protect networks from cutting edge cyberthreats.
Target Audience
Security administrators are responsible for deploying, operating, and managing Palo Alto Networks network security suite.
Enablement Path
This Palo Alto certification path has no prerequisites. Recommended training includes the Firewall Essentials: Configuration and Management (EDU-210) course.
Palo Alto Networks Education
The technical curriculum developed and authorized by Palo Alto Networks and delivered by Palo Alto Networks Authorized Training Partners helps provide the knowledge and expertise that prepare you to protect our digital way of life. Our trusted certifications validate your knowledge of the Palo Alto Networks product portfolio and your ability to help prevent successful cyberattacks and safely enable applications.
MORE RESOURCES
For PCNSA study guide, practice exam questions, and registering for the exam and Palo Alto certification cost in India, ANZ, Americas, EMEA & ASEAN, please refer to PCNSA Certification Page.
OVERVIEW
The Certified Network Security Engineer (PCNSE) exam is a formal certification exam that is hosted and proctored by a third-party testing company, Pearson Vue. The PCNSE exam should be taken by anyone who wants to demonstrate a deep understanding of Palo Alto Networks technologies. This includes anyone who uses Palo Alto Networks products such as partners, system engineers, systems integrators, and support engineers.
PCNSE EXAM OBJECTIVES
The Palo Alto Networks Certified Network Security Engineer (PCNSE) is a formal, third-party proctored certification that indicates those who have passed it possess the in-depth knowledge to design, install, configure, maintain and troubleshoot the vast majority of implementations based on the Palo Alto Networks platform. The Palo Alto Certification PCNSE exam should be taken by anyone who wishes to demonstrate a deep understanding of Palo Alto Networks technologies, including customers who use Palo Alto Networks products, value-added resellers, pre-sales system engineers, system integrators, and support staff.
-
MORE RESOURCES
For PCNSE study guide, Palo Alto practice exam questions, and registering for the exam, please refer to PCNSE Certification Page.
PCNSE FAQS
For additional details about the Palo Alto certifications exams, PCNSE exam, and Palo Alto certification cost, please refer to the PCNSE Frequently Asked Questions list (PCNSE FAQs).
Firewall Training
Configuration and Management (EDU-210)
Get certified and learn from the most experienced trainers. All our trainers are consultants with years of in-field experience
Prisma Cloud
Implementation and Configuration (EDU-242)
Get certified and learn from the most experienced trainers. All our trainers are consultants with years of in-field experience
Panorama
Managing Firewalls at Scale (EDU-220)
Get certified and learn from the most experienced trainers. All our trainers are consultants with years of in-field experience
Prisma Access
SASE Security: Design and Operation (EDU-318)
Get certified and learn from the most experienced trainers. All our trainers are consultants with years of in-field experience
Prisma SD-WAN
Prisma SD-WAN: Design and Operation (EDU-238)
Get certified and learn from the most experienced trainers. All our trainers are consultants with years of in-field experience
Cortex XDR
Prevention, Analysis and Response (EDU-260)
Get certified and learn from the most experienced trainers. All our trainers are consultants with years of in-field experience
Cortex XDR
Cortex XDR: Investigation and Response (EDU-262)
Get certified and learn from the most experienced trainers. All our trainers are consultants with years of in-field experience
Cortex™ XSOAR
Cortex™ XSOAR: Automation and Orchestration (EDU-380)
Get certified and learn from the most experienced trainers. All our trainers are consultants with years of in-field experience
Troubleshooting
Palo Alto Networks Firewall Troubleshooting (EDU-330)
Get certified and learn from the most experienced trainers. All our trainers are consultants with years of in-field experience



